Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

The rise of the Internet of Things (IoT) has transformed everyday objects into smart, connected tools. From voice-controlled assistants to smart thermostats, these devices have revolutionized convenience and automation. However, with great connectivity comes great risk. IoT vulnerabilities are emerging as one of the most alarming flaws in today’s cybersecurity landscape. These weaknesses not only jeopardize user privacy but also threaten entire networks, making IoT security a top concern for developers, enterprises, and consumers alike.

IoT vulnerabilities refer to security flaws in smart devices that can be exploited by malicious actors to gain unauthorized access, manipulate device behavior, or launch broader cyberattacks. These vulnerabilities can stem from outdated firmware, poor authentication mechanisms, insecure communication protocols, and lack of encryption.
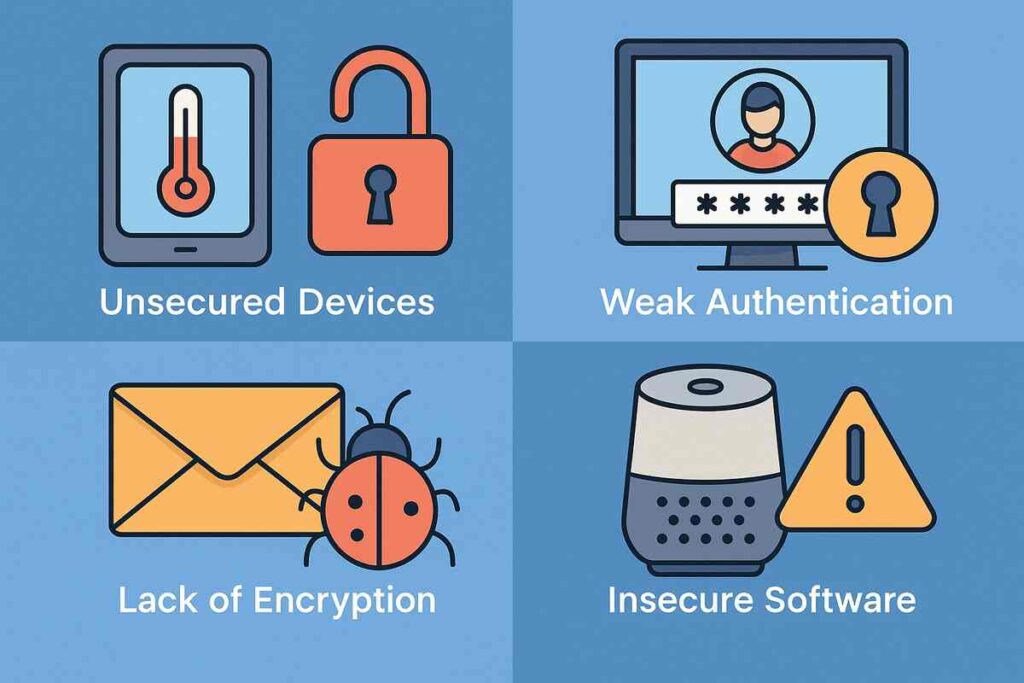
The implications of IoT vulnerabilities are not theoretical—they’re happening in the real world. In one of the most infamous cases, the Mirai botnet attack in 2016 used unsecured IoT devices to execute a massive DDoS attack, taking down major websites and services across the U.S. The attack exploited weak default credentials in connected cameras and routers.
Another example involved vulnerabilities in Ring doorbells, where hackers gained access to video feeds, highlighting how poor security can lead to serious breaches of privacy.
Despite growing awareness, IoT vulnerabilities persist due to several key factors:
IoT device manufacturers often follow inconsistent security protocols, leaving gaps in protection.
In the race to launch products, security is often deprioritized in favor of functionality and cost reduction.
Smaller manufacturers may lack the expertise or funding to implement robust cybersecurity measures.
Consumers rarely update device firmware or change default credentials, unknowingly leaving devices exposed.
Medical IoT devices such as insulin pumps and heart monitors are vulnerable to manipulation, posing risks to patient safety.
Thermostats, lights, locks, and voice assistants collect vast amounts of personal data, making them attractive targets.
Smart factories and infrastructure rely on connected sensors that, if compromised, can disrupt operations or sabotage production.
Connected cars and traffic systems introduce new vectors for cyberattacks that could result in life-threatening consequences.
Cybercriminals exploit IoT vulnerabilities using a range of tactics:
To defend against these threats, stakeholders across the IoT ecosystem must adopt a proactive approach to cybersecurity.
Several technologies and frameworks are gaining traction to combat IoT vulnerabilities:
Blockchain offers decentralized security mechanisms that can validate device identities and ensure data integrity.
Machine learning models analyze behavioral patterns in real time to detect anomalies and potential intrusions.
Automated, encrypted firmware updates ensure devices stay current with the latest security patches.
This model assumes no implicit trust within the network and continuously verifies every device and user.
Governments and agencies are recognizing the dangers of insecure IoT devices. Initiatives like the U.S. IoT Cybersecurity Improvement Act and the UK’s Product Security and Telecommunications Infrastructure Bill aim to enforce minimum security standards.
These measures include:
Organizations that neglect IoT security can face severe consequences:
As the number of IoT devices is projected to exceed 29 billion by 2030, the urgency to address IoT vulnerabilities becomes more critical. Manufacturers, governments, businesses, and users must collaborate to prioritize security at every stage—from development to deployment.
The future will likely see the rise of standardized IoT security certifications, increased investment in threat detection AI, and tighter regulatory frameworks. By aligning innovation with cybersecurity, the IoT ecosystem can achieve both connectivity and safety.
IoT vulnerabilities expose serious flaws that undermine the potential of smart technology. From default credentials to unpatched firmware, these gaps give cybercriminals ample opportunities to disrupt, spy, or steal. As devices become more interconnected, the ripple effects of a single vulnerability can be catastrophic. It is essential to acknowledge these risks and commit to robust, multilayered defenses. Only then can we truly benefit from a connected world without compromising security.